How could a major crypto exchange like Bybit fall victim to the largest hack in industry history? Entering early 2025, cyberattacks surged sharply, highlighting the urgent need to strengthen security for the Web3 community. Hackers managed to steal $1.5 billion worth of Bybit’s digital assets in an incident linked to the Lazarus Group. According to the Hack3d: Web3 Security Report 2024 by CertiK, total losses in 2024 surpassed the previous year’s figures — and this trend continues in 2025, with increasingly intense and alarming attacks.
Based on this data, in this article, AllSpark Research will focus on uncovering Web3 security exploitation patterns and the role of malicious entities like the Lazarus Group. Additionally, this article outlines the precautionary steps taken by the Web3 community to create cybersecurity in a decentralized environment.
1. Web3 Security Threats in 2024 – Trends and Vulnerabilities
Statistics and Attack Patterns
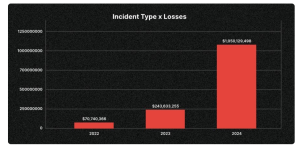
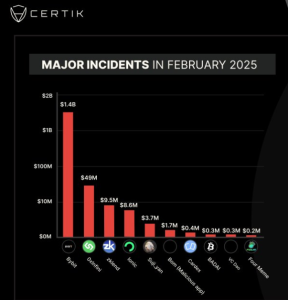
In 2024, CertiK recorded losses of $2.36 billion due to 760 on-chain security incidents, a 31.61% increase in theft value compared to 2023. The rising sophistication of attacks is evident, with average losses per hack reaching $3.1 million, a 23.04% increase from the previous year. Most recently, in February 2025, a cyberattack by the Lazarus Group caused losses of up to $1.5 billion.
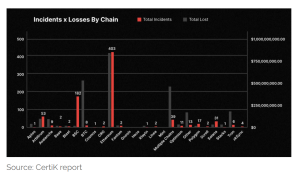
Phishing attacks have become a dominant threat in cyberattacks. Phishing can be likened to a wolf in sheep’s clothing, threatening digital security. Ethereum has been the primary target of phishing attacks, with 403 incidents resulting in losses exceeding $748 million. Ethereum, the second most valuable blockchain by market capitalization, experienced the most hacks, scams, and exploitations.
Technical Vulnerabilities vs. Human Factors
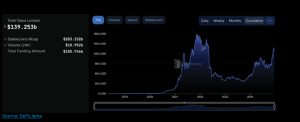
Smart contracts in the DeFi world offer automation and efficiency but also introduce significant cybersecurity risks and technical vulnerabilities. In 2024, the total value locked (TVL) across blockchain networks increased substantially, with liquid Ethereum staking alone soaring from around $248 million in January 2024 to $17 billion in December 2024. This surge in value correlates directly with the potential threat of hacking.
Besides technical vulnerabilities, human factors remain a security gap often exploited. Many users fall victim to phishing attacks through emails or fake websites impersonating Ethereum-based platforms, such as digital wallet imitations or DeFi services. Low awareness of implementing two-factor authentication (2FA) and the lack of habit in verifying URL authenticity further facilitate hackers’ actions.
Suboptimal Global Regulations
Fragmented global regulations on cybersecurity slow responses to cross-border attacks. Asia, particularly Japan, has bolstered its Financial Services Agency. Meanwhile, the European Union has implemented the MiCA framework to stabilize the crypto market.
2. Lazarus Group – The Actor Behind Massive Losses
Profile and Modus Operandi
Lazarus Group is a hacker collective believed to be affiliated with the North Korean government, involved in major cyberattacks since 2009. They typically use tactics like spear-phishing, zero-day exploits, and malware, such as the WannaCry ransomware.
In a recent case, the Lazarus Group laundered 62,200 Ether (ETH) worth $138 million on March 1, 2025, stemming from a massive Bybit crypto exchange hack on February 21. Of the total 499,000 ETH stolen in the $1.4 billion hack, around 343,000 ETH (68.7%) had been moved by the hackers. This case marks the largest exploitation in crypto industry history, more than double the $650 million Ronin Bridge hack on March 23, 2022.[1]
Impact and Global Response
Lazarus Group continues to exploit vulnerabilities like Log4Shell and uses remote access trojans (RATs) written in the rarely used D programming language. The group is also suspected of laundering over $200 million in stolen crypto since 2020.
The FBI responded by blocking wallet addresses and identifying suspicious transactions. Meanwhile, the UN Security Council investigated North Korea’s cyber activities, including those of the Lazarus Group, as part of international sanctions violations. The UN also imposed sanctions by freezing assets linked to the Lazarus Group.
3. Community Actions and the Future of Web3 Security
Preventive Efforts by CertiK and Others
CertiK is strengthening cybersecurity by auditing major projects, revealing critical vulnerabilities, and expanding services. CertiK audited 50% of Web3 projects, uncovering over 115,000 vulnerabilities. The firm also conducted security assessments for Bybit.
Besides CertiK, other parties like crypto exchanges, protocol/blockchain developers, and crypto wallet providers often conduct cybersecurity education. User education includes anti-phishing campaigns, hardware wallet usage guides, and 2FA implementation.
Community Reactions & Regulations
Bybit launched the “Lazarus Bounty” program to involve the crypto community in tracking Lazarus Group’s hacking activities. The crypto community responded positively to this initiative, which offers rewards of up to $140 million for anyone helping track and recover stolen funds. This step demonstrates the collective effort of the crypto community to combat cybercrime and maintain industry integrity.
On the other hand, to support global cybersecurity, the community has developed tools like ransomware decryptors and blockchain analysis platforms, such as Chainalysis, to trace stolen crypto funds. Platforms like VirusTotal also share malware samples for analysis.
In addition to building malware-tracking platforms, the community responds to cyberattacks by creating progressive regulations. For example, Hong Kong implemented stablecoin standards, while the US SEC approved Bitcoin/Ethereum ETFs to encourage transparency.
2025 Prediction: Threats vs. Resistance
Lazarus Group and other hacker entities continue to demonstrate their expertise in stealing and laundering digital assets. They persist in exploiting DeFi and cross-chain bridges, taking advantage of poorly monitored crypto ecosystem gaps. The global crypto community must now be more vigilant against the next moves of these hacker groups.
Security measures and international collaboration across countries are essential to prevent future attacks. Multilateral agreements to prevent state-sponsored hacking, similar to the UN’s proposed cyber treaty, could become a solid foundation for strengthening global digital defenses in 2025.
Conclusion
The sophistication of cyberattacks, such as those carried out by the Lazarus Group, combined with technical vulnerabilities and human factors within the Web3 ecosystem, demands that the community strengthen global collaboration. Without synergy between blockchain platforms, cybersecurity providers, regulators, and users, threats like phishing, smart contract exploitation, and digital asset laundering will continue to haunt the industry. Initiatives like security audits, educational campaigns, and fund-tracking programs are crucial to narrowing hackers’ maneuvering space and protecting the crypto community’s assets.
Without coordinated collective action, trillion-dollar losses due to cyberattacks could potentially recur annually. The Web3 community must accelerate the adoption of progressive regulations, expand cross-border cooperation, and develop more adaptive defense technologies. With this approach, the crypto industry can build a stronger digital fortress and create a safer, more transparent, and sustainable Web3 ecosystem in the future.

